Here’s How to Stay Safe from Online Scams

Online scams are more sophisticated than ever — which means you need to be more vigilant than ever in protecting yourself. From time-to-time, scams like phishing attacks are reported to us at Hostaway.
We want to do absolutely everything in our power to keep you safe. So here’s some important information on how to spot and avoid scams.
Protecting yourself from scams
Part of our commitment to security is making sure you are keeping an eye out for the right things, and taking important steps to secure your account.
Hostaway will never (and we mean never) ask you to:
Share security codes like passwords or 2FA codes
Send bank card details
Transfer money
Use a link in an email or text message to transfer money or share personal details
Share bank or payment details
Make sure you only log in at our official Hostaway website
Scammers will create fake websites to steal your information. These websites often look and feel very official.
That’s why it’s extremely be aware that the ONLY Hostaway website you should ever log into is https://dashboard.hostaway.com
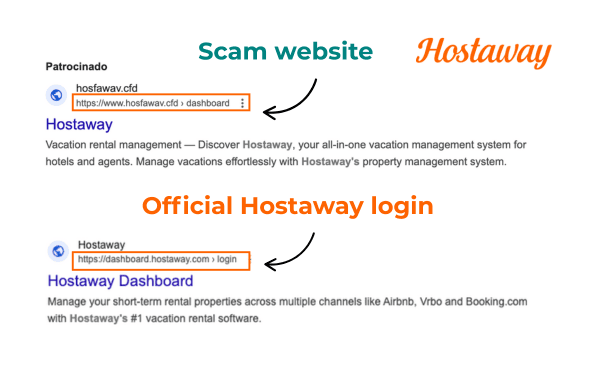
Real examples of scam Hostaway sites
These are real life examples of scam websites whose urls are designed to trick you. If you only do a quick scan of a link URL, you could easily fall prey to these fake websites.
That’s why it’s so, so important to make sure you’re reading carefully and only every logging into Hostaway via https://dashboard.hostaway.com
Always use two-factor authentication (2FA)
2FA adds a layer of security by requiring two different verification methods or factors to access a system or account.
Whether you verify via a one-time code on your mobile device, or via a code sent to a secondary email inbox, 2FA is highly effective in combatting online scams.
(Learn how to enable 2FA for your Hostaway account here.)
Never click on login links from people you don’t know
Be extremely careful in clicking links from unverified emails, unfamiliar websites or social media posts (or just avoid it altogether).
Clicking suspicious links is often all a cyber-criminal needs to get full access to your private accounts.
What to do if you think your account may be compromised
Password reset
If you notice suspicious activity and think your account has been compromised, you should reset your password right away.
But you should ONLY reset your password if you believe your account has been compromised.
Contact your bank
Contact your bank immediately if any of the following applies to you:
You’ve shared credit card details or other sensitive information with someone you suspect is a scammer
You notice a payment or transaction from your back account that you don’t recognize
Contact Hostaway support
If you see something suspicious and need help, you can reach out to Hostaway by email (support@hostaway.com) or via our 24/7 support line. (Here’s a list of phone numbers depending on your location.)
Stay Vigilant, Keep Safe
You have the power to stay safe from online scams.
Ensure you only ever log into Hostaway’s official website (https://dashboard.hostaway.com)
Enable two-factor authentication (2FA)
Don’t ever click links in emails from unverified senders
And in the unlikely event you are affected by an online scam targeting your Hostaway account, reach out to Hostaway Support, available 24 hours a day for assistance.
We’re in this together — and we’re always here to help.